Security and Privacy Management in the Cloud
By: Emiley J in Cloud Tutorials on 2012-10-20
Any application in the SaaS model hast to be designed from the ground up with Security and Privacy in mind. The development strategy starts by understanding the cloud application stack as shown in figure below and identifying the malicious attacker. The attacker can be of two types namely Insider and Outsider.
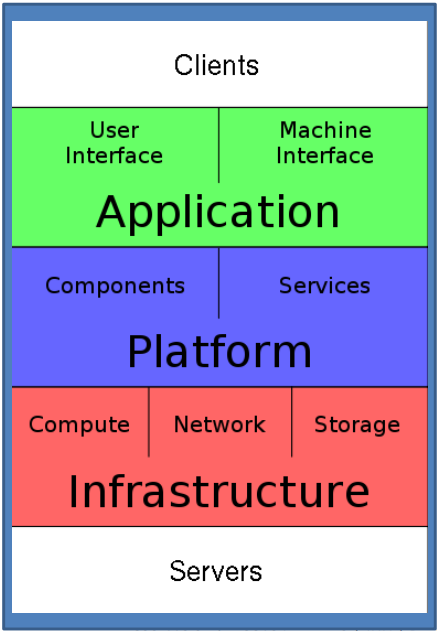
The Insider, can be malicious employees at client, malicious employees at cloud provider or the cloud provider itself whereas the outsider, can be intruders and network attackers.
Malicious insiders could affect Security and privacy by either of these two ways. At client side, the malicious attacker could learn passwords/authentication information or gain control of the VMs by accessing the hosted instances directly. At the cloud side, the operator could log client communications by inside employees.
Malicious insiders at the cloud provider side could read unencrypted data, can possibly peek into VMs, or make copies of VMs or even monitor network communication and application patters.
The motivation of these inside attackers could be to gain information about client data, gain information on client behaviour and then use these information for itself or sell the information.
The outside attacker on the other hand could listen to network traffic or insert malicious traffic, or probe cloud structure or launch a Denial of Service attack. These activities could directly affect the Confidentiality, Integrity and Availability of the services provided.
With this background information you can combat all the identified security and privacy threats by taking the following mitigation techniques.
|
SN |
Common Security and Privacy Threat |
Mitigation technique |
How iConnect4M implements mitigation technique |
|
|
1 |
Spoofing identity |
· Authentication · Protect secrets · Do not store secrets |
Strong authentication technique to be used for the portal and for VMs Key files are used instead of simple username/login. |
|
|
2 |
Tampering with data |
· Authorization · Hashes · Message authentication codes · Digital signatures · Tamper-resistant protocols |
All database related transactions and connections are to be restricted with tamper proof authentication and Security groups are to be utilized to restrict access based on roles |
|
|
3 |
Repudiation |
· Digital signatures · Timestamps · Audit trails |
Audit trails to be captured at every user transaction including admin and super admin activities with timestamps |
|
|
4 |
Information disclosure |
· Authorization · Privacy-enhanced protocols · Encryption · Protect secrets · Do not store secrets |
All important data should be transmitted over HTTPS and SSL. Passwords are to be encoded and cleartext is should not be used or saved. |
|
|
5 |
Denial of service |
· Authentication · Authorization · Filtering · Throttling · Quality of service |
Strong authentication should be imposed for accessing any of the client side applications which prevents unauthorized simulation which should be coupled with monitoring service to alert inadvertent spikes. |
|
|
6 |
Elevation of privilege |
· Run with least privilege |
All root privileges are to be removed from external and role based access and privileges to be imposed at all levels. |
|
Add Comment
This policy contains information about your privacy. By posting, you are declaring that you understand this policy:
- Your name, rating, website address, town, country, state and comment will be publicly displayed if entered.
- Aside from the data entered into these form fields, other stored data about your comment will include:
- Your IP address (not displayed)
- The time/date of your submission (displayed)
- Your email address will not be shared. It is collected for only two reasons:
- Administrative purposes, should a need to contact you arise.
- To inform you of new comments, should you subscribe to receive notifications.
- A cookie may be set on your computer. This is used to remember your inputs. It will expire by itself.
This policy is subject to change at any time and without notice.
These terms and conditions contain rules about posting comments. By submitting a comment, you are declaring that you agree with these rules:
- Although the administrator will attempt to moderate comments, it is impossible for every comment to have been moderated at any given time.
- You acknowledge that all comments express the views and opinions of the original author and not those of the administrator.
- You agree not to post any material which is knowingly false, obscene, hateful, threatening, harassing or invasive of a person's privacy.
- The administrator has the right to edit, move or remove any comment for any reason and without notice.
Failure to comply with these rules may result in being banned from submitting further comments.
These terms and conditions are subject to change at any time and without notice.
- Data Science
- Android
- React Native
- AJAX
- ASP.net
- C
- C++
- C#
- Cocoa
- Cloud Computing
- HTML5
- Java
- Javascript
- JSF
- JSP
- J2ME
- Java Beans
- EJB
- JDBC
- Linux
- Mac OS X
- iPhone
- MySQL
- Office 365
- Perl
- PHP
- Python
- Ruby
- VB.net
- Hibernate
- Struts
- SAP
- Trends
- Tech Reviews
- WebServices
- XML
- Certification
- Interview
categories
Related Tutorials
Power On a VM from ESXI command line
How to change the virtual machine name in Azure
Install OpenStack step by step guide
How to get the API key for CloudStack
HA and DR in a cloud environment such as Amazon EC2
Backup and recovery in a cloud environment such as Amazon EC2
Application Security in a cloud environment such as Amazon EC2
Comments